CyHAZOP – Bringing cyber to the HAZOP
Cyber-security is one of the fastest growing areas of concern for industrial automation and control systems, otherwise known as Operational Technology (OT). As associated assessment techniques and tools continue to be invented, it is worth considering what the tried and trusted Hazard and Operability (HAZOP) study methodology could bring to the cyber world.

The HAZOP has been a staple of the safety industry for decades, providing a familiar, repeatable and effective method to identify and assess hazards affecting the safe operation of process equipment.
The cyber-security industry for OT is still growing and learning; this means there is a lack of accepted risk identification and assessment processes, which in turn drives a lack of consistency. The cyber-security industry uses very different language to that of safety or to business, causing further confusion.
Being well known by system managers and engineers alike, the HAZOP methodology provides a perfect bridge for a comfortable and consistent transition to cyber risk assessment. Utilising the basic HAZOP process concept enables cyber-risk to be assessed in a way that is scalable, can be applied to different industries, and is compatible with a range of security standards and regulatory expectations.
WHAT IS DIFFERENT?
A traditional HAZOP utilises a series of guidewords and process parameters that are combined to create deviations – the ‘No Flow’, ‘Less Flow’, ‘More Pressure’, ‘Less Pressure’ decriptors that all HAZOP attendees will be familiar with.
The Cyber HAZOP (or CyHAZOP) methodology keeps the same basic approach, but with specific tailored guidewords, parameters and deviations designed to target cyber-security needs and enable direct linkage to cyber-security vulnerabilities and controls.
NOVEL NODES
A traditional HAZOP is divided into ‘nodes’, which generally relate to large sections of the process plant and/or where the process parameters remain the same.
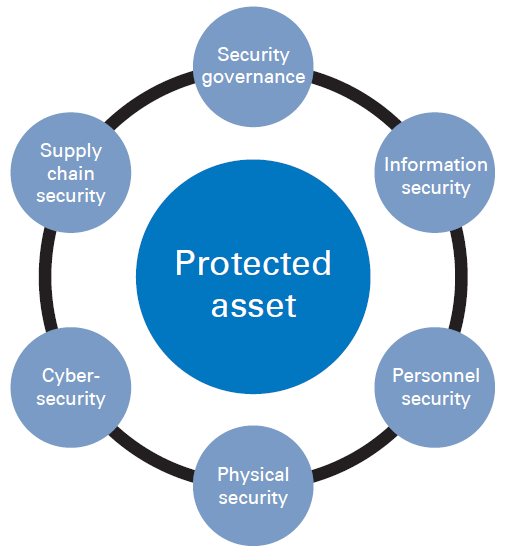
In a CyHAZOP a different approach is taken. The first node is always a contextual view looking at the wider business, to allow the assessor to gain a holistic perspective, incorporating all the security domains shown in Figure 1.
Subsequent nodes are based on Zones and Conduits – the definition of which for most purposes is taken from IEC 62443 (Ref 1), which defines:
- A Zone as a logical or physical grouping of assets within, or connecting to, the system in scope.
- A Conduit as a connection between Zones or between Sub-Zones, concentrating on the data that is exchanged between these Zones.
GUIDEWORDS OR CODEWORDS?
For CyHAZOP, not surprisingly, the guidewords and parameters are also specific to cyber-security; and like nodes, the correlation with conventional HAZOP terminology is somewhat alien.
Zone-based nodes use asset-related guidewords, such as ‘Engineering Workstation’, ‘Control Server’ and ‘Networking Equipment’ to direct the discussion around the types of computerised assets that exist within that Zone.
An accompanying attack-chain set of parameters might be:
- Initial access
- Persistence
- Modification
- Execution
- Recovery
These guidewords and parameters and are then combined to give deviations such as ‘Engineering Workstation – Initial Access’, ‘Networking Equipment – Modification’, which form the basis of the structure for the CyHAZOP Zone assessment.
For Conduits a simple approach is used, the only guideword being ‘Data’, with a standard information security approach for the parameters:
- Confidentiality
- Integrity
- Availability
This gives the deviations ‘Data – Confidentiality’, ‘Data – Integrity’ and ‘Data – Availability’, which prompt the assessment of what happens if there is a lack of data confidentiality, integrity or availability in the Conduit.
More generally, by stepping through each phase of an attack, the types of vulnerabilities, consequences and controls that are used to combat threat activity typical of these phases can be teased out.
LIKELIHOOD AND CONSEQUENCES ESTIMATION
Estimating ‘Risk’ is something that is not always considered within a HAZOP, but when it is, this normally involves the use of a Risk Assessment Matrix (RAM) to determine a likelihood-consequence pairing thus giving a risk level for the scenario under consideration.
Determining the likelihood associated with security risk can, however, be very difficult to quantify. To help solve this, a new technique based on an approach initially presented by Knapp and Langill in 2015 (Ref 2) is used. This employs the DREAD method originally developed by Microsoft (Ref 3) for their Security Development Lifecycle.
For the CyHAZOP, the DREAD model is modified by adding an additional criteria ‘Attack Path Enablement’, to create the DREAAD model (see Figure 2). This ensures that any security factor which enables the attack chain to continue can be captured and allows consideration of the consequences of an attacker achieving their aim in that phase of the attack.

VULNERABILITIES
Vulnerabilities are based around the IEC 62443 Foundational Requirement set, and are kept to a high level, to keep the CyHAZOP efficient and avoid turning it into a detailed vulnerability assessment for each asset. A CyHAZOP will identify areas where more detailed investigations around controls and vulnerabilities should be undertaken.
The CyHAZOP also looks at the consequences of these vulnerabilities being exploited. To do this CyHAZOP takes the MITRE ATT&CK for ICS framework ‘impacts’ (see Ref 4), linking them to the vulnerabilities.
MITRE ATT&CK for ICS is widely becoming the go to method for considering the tactics, techniques and procedures that threat actors can utilise within the OT space. Linking the impacts in this way allows organisations to embed their findings into various third-party process flows for intelligence feeds and vulnerability scans.
CONTROLS
As for a traditional HAZOP, controls are identified to demonstrate the preventative and mitigative measures in place. In CyHAZOP, these are linked to IEC 62443 Security Requirements, which forms the basis for the CyHAZOP control sets.
CONCLUSION
The CyHAZOP methodology is a natural development of the proven HAZOP process and, as such, it offers the same advantages: a systematic and structured technique that actively involves all stakeholders.
In practical applications, CyHAZOP has demonstrated its effectiveness in identifying areas of risk that an organisation is facing within its OT environment. Interestingly, however, one of the biggest benefits seen has been the learning experience that it offers to workshop members.
A Webinar is available on the Risktec YouTube Channel that looks at CyHAZOP in more depth. Click here
This article first appeared in RISKworld 42, issued November 2022.
References
1. IEC 62443 suite. Industrial Electrotechnical Commission. 2007 – 2020
2. Industrial Cyber-security, Second Edition, Eric D. Knapp and Joel Thomas Langill. Syngress, 2015
3. Threat modelling for drivers – Windows drivers | Microsoft Learn https://learn.microsoft.com/en-us/ windows-hardware/drivers/driversecurity/threat-modeling-for-drivers#the-dread-approach-to-threat-assessment
4. MITRE ATT&CK® for Industrial Control Systems: Design and Philosophy, Otis Alexander et al, 2020









