Mapping the Cyber Battlefield
The rise of threat path analysis
As we venture ever forward into a digitalised and interconnected world, it is imperative that we take the necessary measures to protect the systems we rely on. However, with the ubiquity of cyber attacks, how do we go about mitigating cyber threats?

INTRODUCTION
The Operational Technologies (OT) environment continues to be a high priority target for cyber criminals. According to the team at Fortinet, three quarters of OT organisations reported at least one intrusion in the past 12 months (Ref. 1). Recent high-profile penetrations of systems include UK police forces and the UK electoral commission.
So, knowing that, what can we do? Whilst there are many steps in creating a comprehensive cyber security management system, one of the most crucial is understanding the potential threat paths and mapping them out.
THREAT PATHS – WHAT ARE THEY?
Threat paths, also known as attack paths, are described as a visual representation of the events that occur when a threat actor (a person conducting the activity) exploits a threat vector and all the interconnected paths to achieve their outcome, such as a ransomware attack.
A threat vector is the means by which a threat actor gains access to the system. In a physical context this could be going through an open door; in a cyber context this could be accessing an unsecure user account.
Understanding paths and vectors allows us to begin plotting out all the physical, digital and human factor-related connections that will ultimately make up a complete threat profile.
WHAT IS THE BENEFIT OF THREAT PATH ANALYSIS?
Threat paths are designed to give the user a way to visualise an attack considering:
- The technical vulnerabilities of a system
- The human interaction element It enables all the entry points associated with a breach to be identified as the hypothetical attack is developed.
This visualisation in turn provides a more detailed understanding of existing vulnerabilities while allowing a holistic view of how they could potentially be mitigated.
PHYSICAL SECURITY
In the physical world, a threat path is easier to comprehend. It is the path an attacker could take from the border of your facility or from a public area in your facility to the room containing the equipment they wish to compromise. Determination of such paths allows a security professional to place security measures along that path to detect, mitigate or prevent the attack from succeeding. Such security measures could include physical access controls (i.e. doors and walls), CCTV monitoring of approaches and the positioning of security checkpoints to screen all persons passing through the area.
Even in large sites with complex facilities and targets across multiple buildings and multiple floors, clear entrances and choke points, such as stairs, lifts and doors, can be identified for suitable protection. A number of computer programs are available to automatically determine routes from access points to target areas; or in simple cases the assessment can be performed manually using target locations and facility floor plans.
CYBER SECURITY
In the cyber world, there are many variations of cyber security threat paths, with each path unique to the environment under consideration. However, there are some good frameworks that can be used.
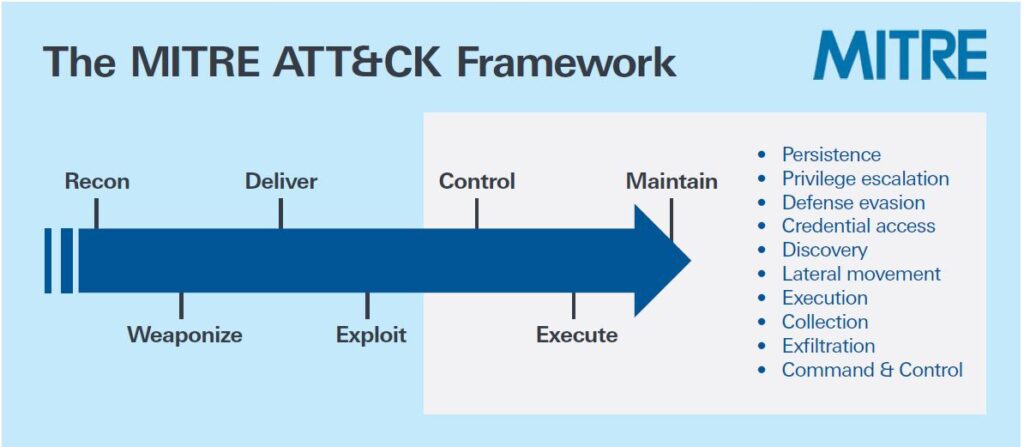
A useful resource for considering threat vectors is the MITRE ATT&CK model (Ref. 2 and Fig. 1), which gives example techniques used by attackers. When you combine this with your own system model, the user can begin to identify their key nodes and the associated potential vulnerabilities.
Alongside this, there are many tools available which can support threat analysis, such as the Microsoft threat modelling tool (Ref. 3) which is a free to access platform. Although not necessarily as comprehensive as the MITRE ATT&CK model, it is contained in a user-friendly environment and covers six areas known as STRIDE: Spoofing, Tampering, Repudiation, Information disclosure, Denial of service; and Elevation of privilege.
With the MITRE ATT&CK model and Microsoft threat modelling tool (or one of the many other threat path analysis tools available), it is possible to start answering the question, “Is my cyber system secure?”
WHERE TO START?
When considering threat path analysis, the user needs to consider the initial source of compromise. How would an attacker get in? To answer this, it is essential that a clear understanding of the system architecture is available. Then it’s time to look at how the attacker might gather information and move around the system. This process could involve mapping out the interconnection points, such as physical entry, digital entry, human factor weaknesses, and so on. Considerations should include the motive of the attacker: What might they be targeting, what might they be trying to achieve and how would they go about it?
The last part of the puzzle is to predict how an attacker might cover their tracks, what would they need to do to prevent detection during the attack or after they have achieved their goal. With all these thoughts in mind the user will be in a strong position to build their threat paths and to develop some of the mitigation strategies that may be required to strengthen their security position.
CONCLUSION
It is impossible to protect systems and their parent facilities against unidentified security risks. To help counter this, conducting a threat path analysis exercise provides an end-to-end view of the threats and the extent of their interconnection, while identifying the vulnerabilities and suggesting means of mitigation along the way.
With ever-developing technological advancements it is now more essential than ever to pro-actively map out the security weaknesses of our digital world to ensure that appropriate levels of protection are in place.
This article first appeared in RISKworld Issue 44
References
- Fortinet Press Release, Fortinet Global Report Finds 75% of OT Organizations Experienced at Least One Intrusion in the Last Year, 24 May 2023
- https://attack.mitre.org
- Microsoft Threat Modeling Tool, https://learn.microsoft.com/en-us/azure/security/develop/threat-modeling-tool