Safe and Secure? The Integration of Safety and Security
The emerging terrorism threat worldwide, and in particular, the threat from the well-informed insider wanting to do harm and willing to die for the cause, is challenging conventional security practice at high hazard sites and public places. To counter this threat, industry has responded with discrete security enhancements which can often result in conflict with safety requirements. This is well illustrated by the recent Germanwings tragedy, where enhanced cockpit security measures enabled the pilot to deliberately crash the plane.
COMMON GOALS
Developing effective security requires an ever greater understanding of the operations within a high hazard site in which critical assets are identified and proportional security measures are applied for their protection against a range of credible attack scenarios. This is akin to the approach followed in safety cases in assessing and mitigating the risk across the range of major accident scenarios.
Since security and safety share the common aim of protecting people, safety-critical assets tend to be security-critical assets. Hence, having a common approach to security and safety would introduce consistency and, if integrated, would naturally identify and manage conflicts, as well as realising efficiency savings.
The concept of integrated security and safety has been around for some time, and it is interesting to note the lead taken by the UK’s Office for Nuclear Regulation recently in the integration of its safety and security regulatory organisation. However, the delivery of integrated safety and security by industry has been slow, predominantly because of the different approaches taken by the two sets of practitioners, and the higher levels of security clearance required for some of the more sensitive activities. Furthermore, security has tended to be more prescriptive than the risk-based practice of safety and also communication around security tends to be on a need-to-know basis whereas safety emphasises widespread, open communication.
BOWTIE ANALYSIS
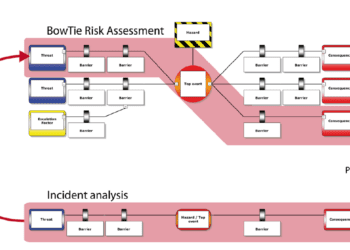
Recognising these differences, a workshop-based approach can form an effective basis for the delivery of an integrated safety and security solution. This is illustrated in Figure 1 using the bowtie approach in which safety and security is also integrated with environmental protection.
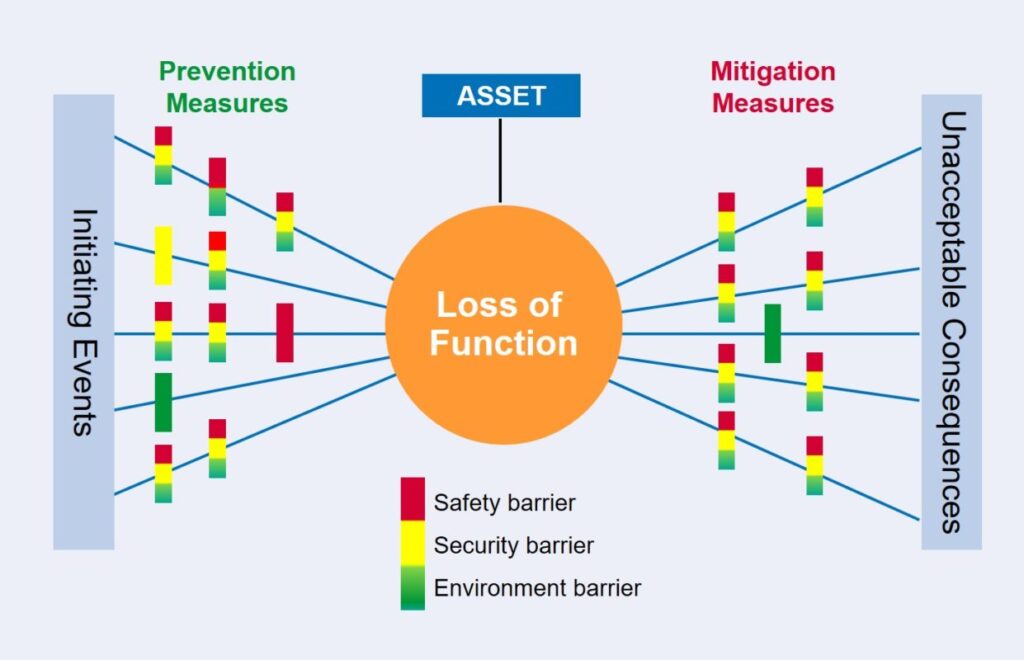
Figure 1 – Bowtie assessment of safety, security and environment
Attended by safety, security and environmental practitioners, as well as designers and operators, the workshop would establish potential initiators that could start a chain of events leading to unacceptable consequences, the preventive and mitigative barriers and their functional requirements. For barriers delivering multi-functions, any conflict between safety, security and environmental functions is readily identified and can be deconflicted by the assembled team.
The bowtie approach facilitates a greater understanding of the operations and hazards, enabling the development of proportional, asset-specific security management arrangements to protect against credible attack scenarios, including the well-informed insider. This, and the interface between security and safety, also support future security reviews and ensure that meaningful, safety-informed, security enhancements are delivered.
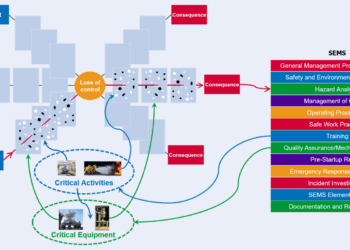
This philosophy of integration can be extended to put in place an integrated operational management system, as illustrated in Figure 2, noting that the barriers may be plant, processes or people. An integrated management system would have the clear benefit of avoiding ambiguity and delivering efficiency savings for those barriers that deliver a combination of safety, security and environmental (SSE) functions.
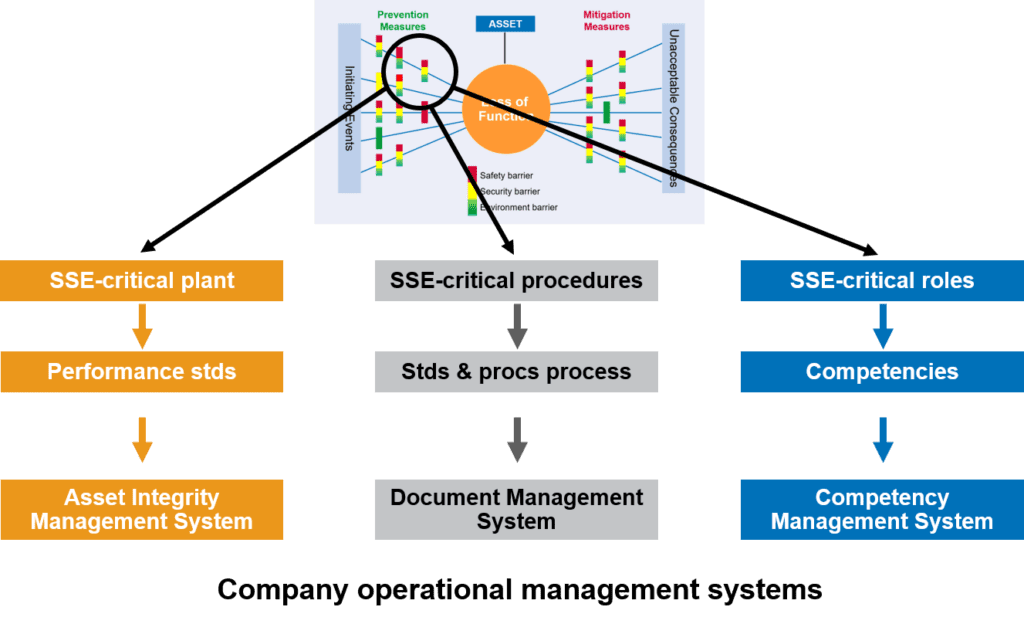
Figure 2 – Integrated operational management system
CONCLUSION
In a world where security threats appear to be constantly evolving and resources are becoming more and more stretched, the integration of safety and security makes sense on a number of levels, from improving understanding to the effective and efficient provision of security measures.
This article first appeared in RISKworld issue 28